The next generation firewall (NGFW) market is anticipated to grow to $4.3B by 2022. Market growth is now being fueled by cloud appliances, small to medium enterprise adoption, and IoT / BYOD device explosion. These forces are leading to a sales bonanza for NGFW vendors. After all, deep packet inspection for complex security decision-making is tough stuff. It requires specialty silicon, monolithic software, and steep vendor support hand-holding. Translation? Expensive.
Is there an alternative? Yes. It’s called an open-source NGFW. What? All of those complex DPI, IDS/IPS, app control, packet filtering, email security, threat protection / sandboxing, and traditional firewall features available through open source? And at serious speeds like 1, 10, or 100 Gbps speeds? Pipe dream. Or is it?
It’s closer than you think. Clearly, many security applications have long been available in open source: Snort, Nessus, Metasploit, NMap, Wireshark, OpenSSH, etc. But packaging them for speed, scale, defense-in-depth integration, and ‘1-800-help_me_tune_this_nightmare’ has remained the domain of proprietary vendors, who often demand a small ransom. Well, the times, they are a changin’.
Enter open-source, high-performance packet processing software from the Linux Foundation’s fast data plane project, FD.io. Now packet processing speed, scale, efficiency, and software defined flexibility for networking and security functions can be performed ‘fast, good and cheap’ - across bare metal, VM, and container deployments.
It’s a story your CEO, CIO, and CFO will all love, and Netgate® TNSR™ makes it real.
TNSR (pronounced “tensor”) is an open source-based secure networking software platform. At its core is a Vector Packet Processing (VPP)-based high-speed packet processing engine. It enables secure networking at speeds of 100+ Gbps - at a fraction of the price of proprietary alternatives. TNSR is also extensible well beyond Netgate’s traditional business of firewalls, VPNs and routers. TNSR can enable entire security stacks to perform reliably at speed - and at very low cost.
One example of its extensibility is in the world of IDS/IPS. With TNSR, packet processing can be scaled easily to any level of bandwidth inspection on commodity silicon. Further, as a software-defined device, TNSR can easily be administered via a RESTCONF API. For example: Adding ACL block rules in response to alert messages received from a Snort IDS instance is a virtual walk in the park.
Our TNSR-IDS project does exactly this. The short description is that a port mirror is set up to pass a copy of the traffic from an interface to Snort. TNSR-IDS analyses the alert messages from Snort, constructs ACL block rules and automatically installs them in TNSR via the RESTCONF interface. Our recent Cloud Mirror Port TNSR video provides a high-level demonstration of how to accomplish diagnostics and security, like IDS, in a separate VPC on AWS.
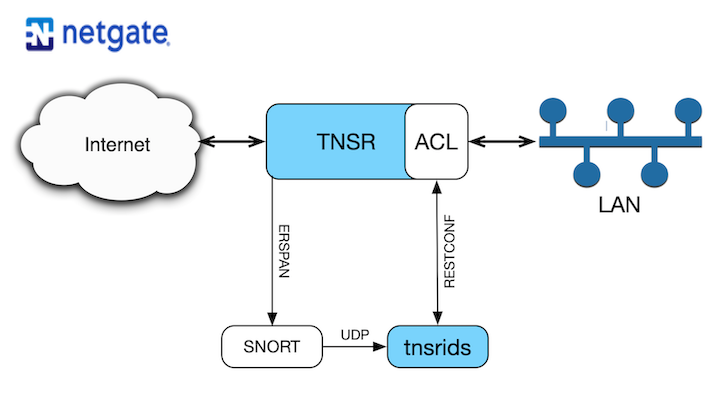
TNSR-IDS is written in the Go programming language, allowing it to be easily compiled for a large number of OS and architectures. Details, source code, and setup instructions (including TNSR, SNORT and ERSPAN) can be found at the TNSR-IDS Project GitHub Repository. A README file is included in the repository that provides a lot of detail about the process, as well as a TNSR-Snort setup file that gives detailed installation instructions.
Whether your requirements are in the cloud or on hardware, TNSR’s high-speed, extensible, packet processing capabilities can give you next-gen capabilities without gouging your budget.
-01.png?width=926&height=181&name=Netgate%20Logo%20PMS%20(horizontal)-01.png)
%201.png?width=302&name=Netgate%20Logo%20PMS%20(horizontal)%201.png)