Packet Capturing¶
Capturing packets is the most effective means of troubleshooting problems with
network connectivity. Packet capturing, also known as “sniffing”, shows packets
“on the wire” coming in and going out of an interface. Observing how traffic is
sent and received by the firewall is a great help in narrowing down problems
with firewall rules, NAT entries, and other networking issues. pfSense®
software includes a GUI page that captures packets using tcpdump in an easy
manner. The tcpdump utility can also be used at the command line in a shell,
and alternately, packet capturing can be performed by Wireshark.
Capture frame of reference¶
Keep in mind that packet captures show exactly what is on the wire. A packet
capture is the first process to see traffic when an interface receives a packet
and it is the last to see traffic when an interface sends a packet as it flows
through the firewall. It sees traffic before firewall rule, NAT rule, and all
other processing on the firewall happens for traffic coming into that interface,
and after all that processing occurs for traffic leaving that interface. For
incoming traffic, captures shows traffic that arrives on an interface on the
firewall regardless of whether that traffic will be blocked by the firewall
configuration. Figure Stack Processing Order illustrates where
tcpdump packet captures tie into the processing order.
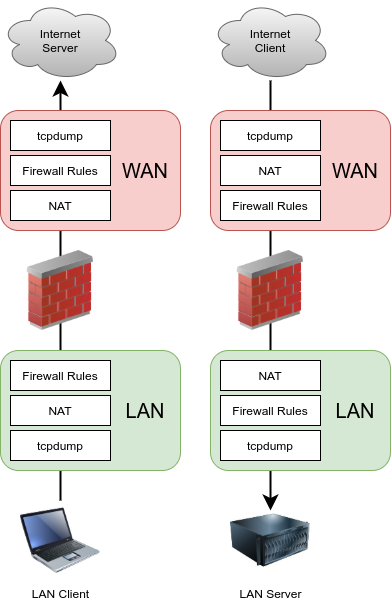
Stack Processing Order¶
See also
Ordering of NAT and Firewall Processing explains how the firewall processes connections in greater detail.